3.4 KiB
| title | summary | date | lastmod | categories | tags | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| Stalled SSH connections | My pfSense removed valid connections obviosly. This is how I solved it. <small>The thumbnail was created with Google AI (Imagen 3).</small> | 2024-10-06T19:30:17+02:00 | 2025-01-12T16:24:13+0000 |
|
|
I spent some time adjusting my SSH configuration because I often get stalled connections to my servers but I never got that fixed until recently, when I started looking in my firewall settings on the pfSense.
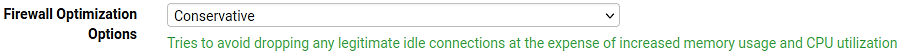
After changing the Firewall Optimization Settings within System → Advanced → Firewall & NAT to Conservative I had no more of these hangs of my SSH sessions.
I use the ControlMaster setting in my SSH configuration so the stalled
connections have to be killed with something like
$ ssh -O exit {short hostname}
every time -- which is annoying.
{{< alert "triangle-exclamation" >}}
Update on December 17 2024:
A few changes to the SSH configuration on client and server have been made.
{{< /alert >}}
It got better, but I still experience the one or other hang.
I added/modified these entries within Host * in
~/.ssh/config on the client:
ServerAliveInterval 100
ServerAliveCountMax 10000
and made these changes/additions in /etc/ssh/sshd_config on the server:
ClientAliveInterval 60
ClientAliveCountMax 10000
TCPKeepAlive yes
{{< alert "triangle-exclamation" >}}
Update on January 5 2025:
Another change to the firewall setup in my home network.
{{< /alert >}}
I did not had this on my mind but I accidentally saw my firewall retrieving a blacklist from my server and like instantly my ssh session was unusable again.
I now reduced the amount of updates the firewall retrieves the blacklist and hope for the best!
{{< alert "triangle-exclamation" >}}
Update on January 12 2025:
The final solution should be the removal of all IPv4 based blocks
{{< /alert >}}
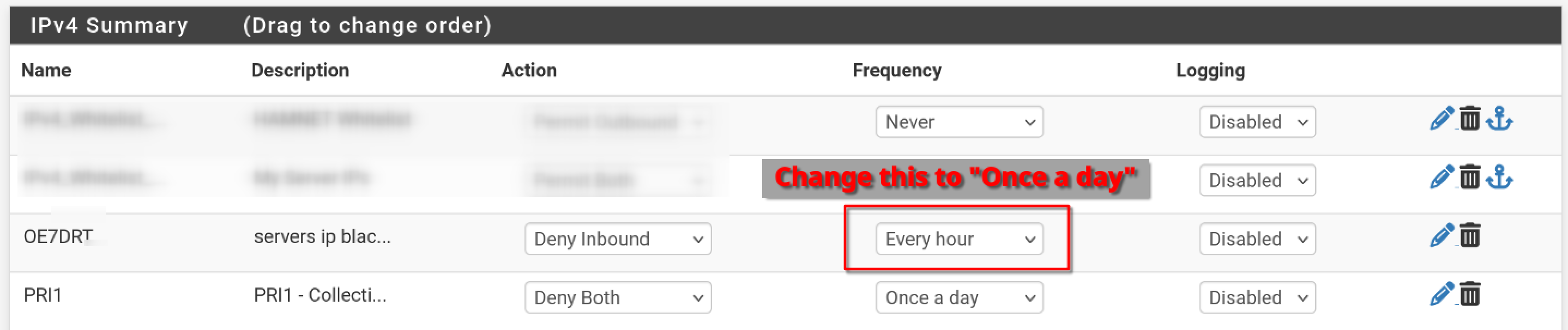
As the logs of the pfBlockerNG indicate: every hour runs a job that fetches and updates blocklists for IP and DNS based blocking (if neccessary).
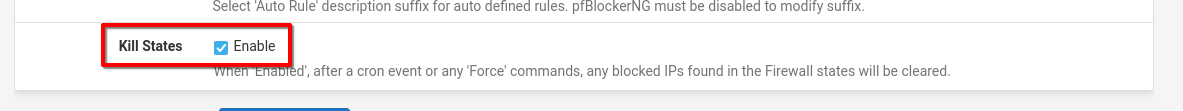
Since the script kills all states to IP addresses in these lists my guess was, that I should remove these types of blacklist (as the firewall blocks incoming traffic of unknown sources anyway).
I'm not sure how my servers IP got there, but I think the script kills all states of any addresses listed in these lists, including those in whitelists.
[ pfB_Top_v4 ] Removed 46 state(s) for [ 89.58.16.xxx ]
igb1 tcp 89.58.16.xxx:ssh <- 192.168.11.yyy:53226 ESTABLISHED:ESTABLISHED
igb0 tcp 192.168.31.zzz:25103 (192.168.11.yyy:53226) -> 89.58.16.xxx:ssh ESTABLISHED:ESTABLISHED
igb1 tcp 89.58.16.xxx:ssh <- 192.168.11.aaa:49270 TIME_WAIT:TIME_WAIT
igb0 tcp 192.168.31.zzz:36706 (192.168.11.aaa:49270) -> 89.58.16.xxx:ssh TIME_WAIT:TIME_WAIT
... and so on etc ...
Maybe it would have been enough to stop killing states but as I already wanted to thin these lists anyway...
Otherwise this settings should suffice, theoretically: